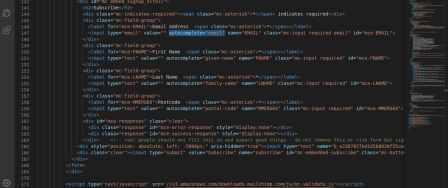
There is lots of advise on how to disable autocomplete, or copy/paste for input forms especially password forms. This is mostly well meaning, in that there is a perception that this makes their sites more secure, when in practice this makes them less secure.
The correct security advice is to recommend that users use a password manager, and that the web-page assists the password manager by setting the autocomplete="current-password" on the field so that users can use long, complex, randomly generated, and unique passwords to log in quickly.
If you make the user type the password they will
1. hate you
2. use a simple easily remembered password (weak, not unique, & short)
3. users that already use a password manager will give up and go elsewhere
autocomplete="off" is almost universally ignored by browsers, and is always ignored by password managers. Some password managers have an option to respect autocomplete, but if you turn this on it makes the password manager useless.
if autocomplete="off" is set the password manager has to guess which fields are which on the form. They do this by looking at the field name, the input type, and the label fields. But there is no standard as to how these are named.
Perhaps the most unfathomable aggression against the user is this plugin:
The jquery.disableAutoFill plugin randomizes an input’s name attribute by default. When the form is submitted, the plugin restores the original name. This prevents auto-completion for all browsers (includes third-party auto-completion extensions) but doesn’t necessarily help with login fields. https://terrylinooo.github.io/jquery.disableAutoFill/
On the Mozilla page about autocomplete it tries to remind developers about the principals of what the web is for:
It is important to know that if you turn off autocomplete, you are breaking the rule 1.3.5: Identify Input Purpose in WCAG 2.1. If you are making a website that should follow WCAG, you should use autocomplete with autofill. https://www.w3.org/WAI/WCAG21/Understanding/identify-input-purpose.html
https://www.ncsc.gov.uk/blog-post/let-them-paste-passwords
https://developer.mozilla.org/en-US/docs/Web/HTML/Attributes/autocomplete
https://developers.google.com/web/fundamentals/design-and-ux/input/forms



 Posted by Stuart Ward
Posted by Stuart Ward 
 Using a text message (SMS) to deliver a authentication or security token to a user has been useful in the past. It is still used in many systems, but we need to phase this method out.
Using a text message (SMS) to deliver a authentication or security token to a user has been useful in the past. It is still used in many systems, but we need to phase this method out.